I had been in IT for extra than 20 years, but have in no way had any arms-on involvement in booths. Adroitly, I realize what they may be and the way they paintings, but due to the fact that I’ve in no way had to execute them, I didn’t recognize the way it worked. Also, I had no clue approximately the way to clearly make certain approximately them. Once extra, the concept sounds first-rate, but the acquainted pronouncing of “as protection builds, comfort diminishes” sat in my mind, and with how easy the whole thing compartment associated sounded, it likewise regarded as even though protection might have been a piece of hindsight.
Turns out I turned into correct.
To discover a plausible pace, I pursued the Black Hat 2020 assembly entitled, “From Zero to Hero: Pentesting and Securing Docker Swarm and Kubernetes Environments.” The route, knowledgeable via way of means of Sheila A. Berta and Sol Ozan, sincerely started with a portrayal of the way Docker booths functioned and went totally via a Kubernetes association. It turned into altogether involved – understudies had been required to introduce Docker and microk8s on their very own device earlier than the class – and turned into a first-rate approach to understand how the apparatuses impart, wherein the frail focuses are, and in particular, the way to take a stab at securing it.
Lamentably, whilst the route says you’ll be a “legend” in the direction of the end of days, I even have a tendency that I am truly starting now no longer a long way off and feature a lot extra to learn. All matters considered, I wasn’t going into it hoping to be a consultant after simply sixteen hours of preparing.
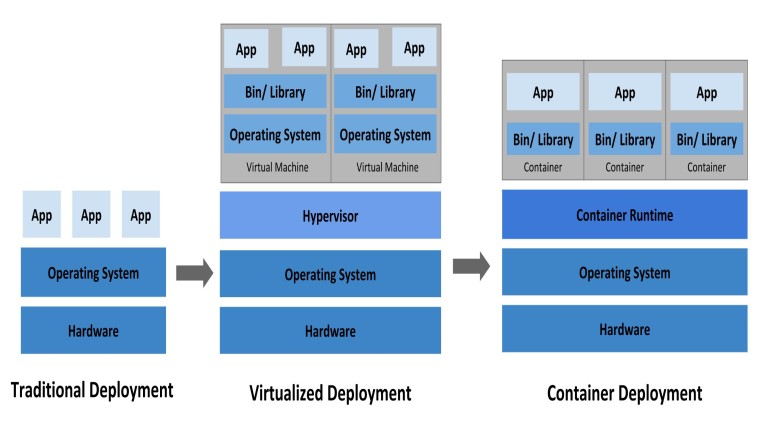
Before stepping into my tremendous stage perceptions, it’s important to make clear what a compartment is. In the development world, it’s now no longer sudden to compose code to your very own device, have it paintings impeccably, but then whilst you deliver jogging it a shot an employee a few places, it truly doesn’t paintings. Compartments try to defeat that difficulty via way of means of giving impartial machines that you may without a lot of a stretch port beginning with one employee then onto the following and also you recognize it’s going to constantly paintings. Like the call infers, it consists of everything of the code, libraries, and programming predicted to run. Kubernetes, then again, is an associate degree for booths. Essentially, it helps you to oversee masses or hundreds of numerous booths in a steady way.
The following are a part of my takeaways from each a Red Team and Blue institution viewpoint.
Red Team
Most holders run matters as root: This implies at the off threat which you are good deal a host, you’ll probably have a complete manage of the compartment. That makes the accompanying ranges considerably simpler.
The docker. Sock Bind Mount is hazardous: If you’re root in a holder and introduce Docker in a compartment that has a Docker attachment (var/run/docker.Sock), you’ll have the choice to evaluate the complete institution, which includes getting a shell inside a few different compartments. By then, not one of the gadget department or extraordinary controls will stop get to.
Condition elements often incorporate insider facts: In severe cases, people ship passwords into the holder utilizing simple situation elements. So with inside the occasion which you technique the record, you may see the earth elements and in addition make bigger your forces.
The Docker API can deliver a ton of data: The Docker API, naturally, is unauthenticated and might discover a ton of data. Utilizing Shodan, you may without a lot of a stretch find out a rundown of open ports and from that point, can get insights regarding the bunch and flip to taking it over totally. Pattern Micro has charming weblog access approximately the point.
Blue Team
Try now no longer to run matters with inside the holder as root: While it’s whatever however tough to run matters as root, you shouldn’t do it. Rather, display packages with decrease concur to making plans the UID via way of means of both utilizing the – patron order line preference or via way of means of utilizing the USER mandate with inside the docker file.
Try now no longer to allow holders to introduce matters: Almost every attack started with us introducing something. From nmap to config to Docker itself (withinside the compartment), status quo of something withinside the holder turned into a repeating theme. This is the purpose you have to constantly prevent any unused ports at your limit. This likewise forestalls Command and Control correspondence at the off threat that someone taints your device. Notwithstanding forestalling the status quo of devices, you have to likewise make certain the holder itself has simply the bottom quantity of makes use of delivered to anyways perform its responsibility.
Ensure the Docker Socket: The Docker attachment is the way via way of means of which correspondence is handled amongst holder and institution, so it needs to be secured. While I won’t extensively expound right here, the Docker internet site web page has what offers off the influence of being a first-rate article specifying the way to steady it.
Use Docker Secrets as opposed to situation elements: Docker Secrets has been round due to the fact that 2017. While now no longer steady, it’s regardless of the whole thing higher than utilizing situation elements to byskip privileged insights into the compartment.
In the occasion that this has crowned your hobby on booths, you may introduce Docker and moreover Microk8s (a bit shape of Kubernetes) fairly with none problem. Here are the status quo pointers for introducing Docker on Linux or MacOS, and right here are the status quo instructions for introducing Microk8s on Windows, Linux, or MacOS.
When the status quo is finished, the Docker has a pleasant “Snappy Start” manipulate on their site, and MicroK8s has one for his or her object too.